Privacy Management
Use CGR Foundation to build an integrated privacy management system tailored to your business processes, the jurisdiction you operate in and the service you provide.
Tailor a comprehensive privacy management system to suit your business needs
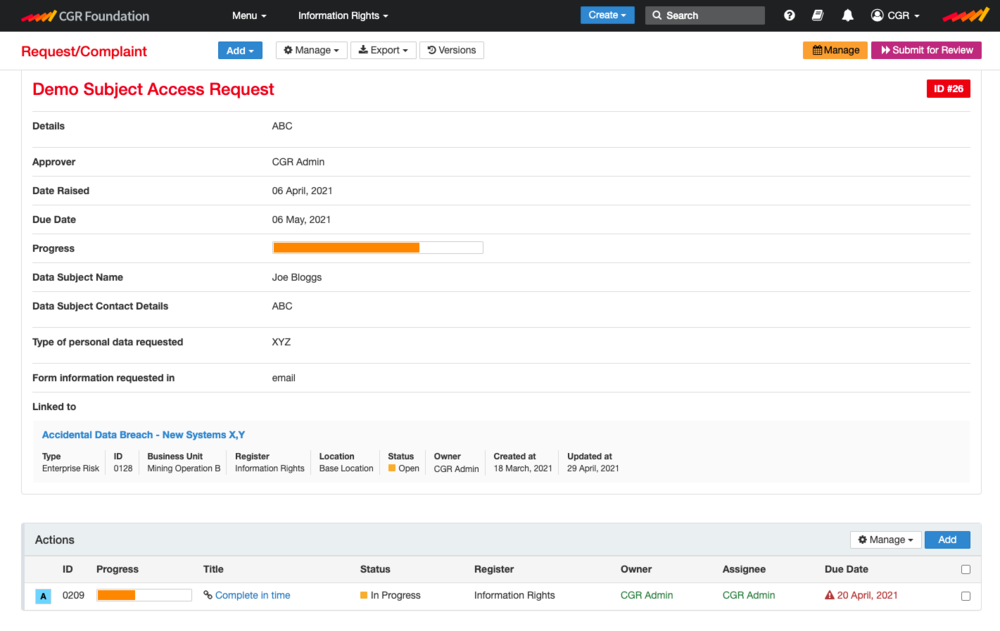
Data Requests
Deal with Subject Access or Freedom of Information Requests quickly and effectively. The requests can arrive in CGR Foundation automatically from an external form on your company website (with notifications) or you can enter them directly. Assign ownership and actions as required to meet the closure deadline, thus retaining the records of your response easily to hand.
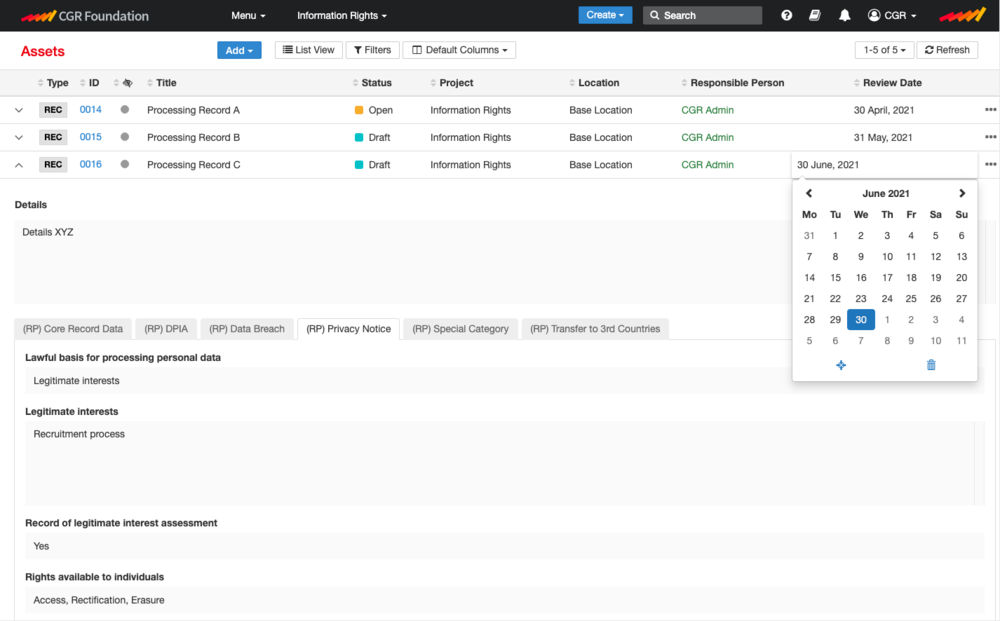
Data Processing
Create and maintain Records of Processing and Information Asset registers. Make the capture and review of these records a consistent and repeatable process. Create confidence that the personal data you hold is on the right legal basis and that the evidence is available at your fingertips. Assign actions and hold people to account where you need and have your response to due diligence ready.
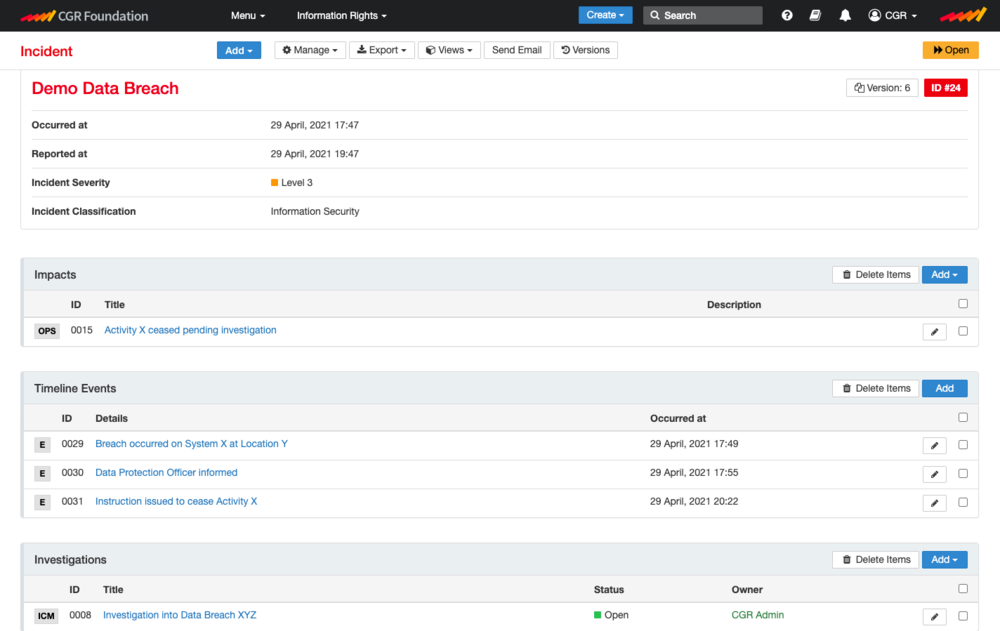
Data Breaches
If a breach occurs, let CGR Foundation help you manage it in a compliant and professional way. Track and manage your response steps, from notification of data subjects and regulators to investigation and implementation of findings. Where organisational changes are necessary, use the system to manage them with evidence. Minimise reputational damage and sanctions, exploit the opportunity to improve and engage.
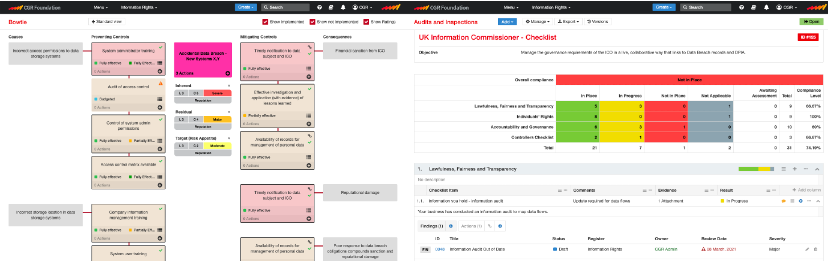
Data Risk and Compliance Management
Use CGR Foundation to analyse and manage your privacy management risks – particularly for Data Protection Impact Assessments when planning a new process or project. Use CGR Foundation to tailor your audit and compliance management, using system links to risk assessments for a risk-based audit approach.
And more with standard features
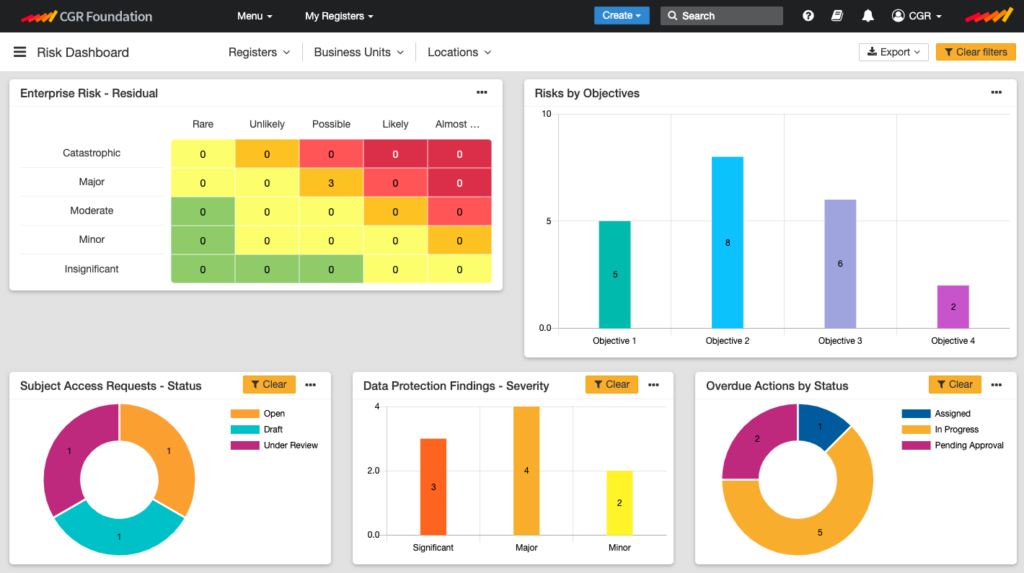
Privacy Management Picture
Use dashboards to bring your Privacy Management System to life in a clear and focused single version of the truth, giving you access to the information required for effective decision-making.
Key Features
System Agility
Integrate privacy with information security – use system agility to manage asset confidentiality, availability and integrity. Manage ISO27001 or NIST controls, and security event reporting.
Workshops
Conduct your Data Protection Impact Assessments in a collaborative way. Use the Workshop module to build a live assessment, with an integrated record of attendance and decisions.
Notifications
Don’t miss Subject Access Request deadlines. Use the system to manage the reminder burden – tailor the frequency and distribution of notifications to your organisation.
Go Further
Use reporting to show your response time trends for Subject Access and Freedom of Information Requests. Drive improvements over time and export the metrics to impress your stakeholders.
And more with standard features
Industries where you’ll find us
“Isn’t having customers’ trust a cornerstone to good business? Isn’t that intangible relationship with customers (loyalty, trust, repeat customers) something most companies want?”
— UK Information Commissioner, from a speech to the Chartered Institute of Accountants, 17th January 2017



